TOPDOWN WHITE PAPER
Topdown deploys INTOUCH® as a multi-tenant Software-as-a-Service (SaaS) solution on top of Amazon Web Services (AWS) for a 100% cloud-based customer communications management solution. Under the resulting shared responsibility model, Topdown manages the security of the INTOUCH application that sits on top of the AWS public cloud platform.
What outwardly appears to be a cohesive, monolithic application is, in reality, a collection of services and microservices that are Topdown information technology (IT) assets. This document details the security principles and practices we employ to protect those assets.
NOTE: Any AWS-provided tools and services we use are indicated in Amazon orange.
Securing IT assets requires knowing what they are and how they are used. IT and admins should not have to guess what their IT inventory consists of, who is accessing those resources, or what kinds of actions users execute on these resources.
Audit and trace are tools that track and monitor AWS-based resources, so we have instant visibility into the inventory as well as user and application activity. For example: with audit and trace tools we can discover existing AWS resources, export a complete inventory of AWS resources with all configuration details, and determine how a resource was configured at any point in time. These capabilities enable compliance auditing, security analysis, resource change tracking, and troubleshooting.
Furthermore, audit and trace security principles identify the requirements to understand, on an ongoing basis, if the necessary mechanisms are in place to continually protect data and the assets storing or processing that data. Audit and trace:

INTOUCH employs a comprehensive monitoring and logging system, extremely important for compliance with internal policies, industry standards and legal regulations.
See the technology overview for details on the tools INTOUCH uses for logging and monitoring.
In addition to low-level monitoring and logging, INTOUCH retains a record of all end-users actions made in the user interface (e.g., creating or editing an asset) and maintains a complete history of all sent communications.

Data availability is of paramount importance in the cloud. The AWS platform was engineered from the ground up to provide resilience from attack. Topdown leverages AWS tools and services to see exactly what is happening in the AWS environment.
INTOUCH implemented the primary application layer/intrusion detection protection with the AWS Web Application Firewall (AWS WAF) that protects web applications from common exploits such as distributed denial of service (DDoS) attacks that could affect application availability, compromise security or consume excessive resources.
AWS WAF also delivers control over which traffic to allow or block to web applications by defining customizable web security rules. Topdown uses AWS WAF to create custom rules that block common attack patterns, such as SQL injection or cross-site scripting, with additional rules designed for application specifications that can be deployed within minutes for quick respond to changing traffic patterns.

Definition: a set of procedures designed to bypass the security controls of an IT system in order to test that system’s resistance to attack. Essentially, it is a form of ethical hacking to identify and assess vulnerabilities in computer systems before the wrong people find them. A pen test is a key requirement in determining whether security policies are effective, as well as an essential component for maintaining compliance.
Topdown performs regular pen testing to provide tenants with the confidence that systems are secure from attack and to provide reassurance to tenants’ customers that their data are adequately protected.
A network pen test (also known as an External Network Security Assessment) is an external penetration test that identifies the vulnerabilities of computer systems through their exposure to the Internet. We perform network penetration tests on the following devices and systems:
Topdown looks for potential exposure across the various web sites, extranets and intranets for application layer vulnerabilities to test applications for:
Developing an incident response strategy for our cloud-based environment is different from developing one for traditional, on-premises environments.
An incident response strategy typically includes the following phases:

To anticipate and deter security incidents, Topdown incorporates common security best practices—including AWS security design principles—as outlined by the Topdown Information Security team as well as common regulatory practices as defined by governance and compliance standards.
A comprehensive logging methodology delivers critical information at every phase for a robust incident response strategy including access, application, system, event, API call, and database logging.
Topdown leverages tools and features that automatically collect and store logs from different application components and infrastructure resources.
Topdown is always prepared to restore resources quickly with automation templates synchronized to the infrastructure that avoids manual patching. Should a change in configuration be needed, the configuration management tools can replace an instance on a short notice, or deploy a new stack if required.
With a well-practiced plan of tactics and playbooks, the Topdown incident response team can execute the plan rather than try to improvise under the stress of an attack.
A vast array of data flows within the INTOUCH solution, including (but not limited to):

General object storage contained herein; partitioned by realm and access to those items defined in a realm; restricted to only those users or transactions authenticated to that realm. The Asset Library maintains the base toolkit that tenants use to define the design and content of their communications, including both rules and definition of data items.
Stored in the Asset Library within a folder-like structure; the structure and objects are defined within a DGraph graph database that maintains the relationship between folders and objects, as well as between objects (content used by template, etc.). The graph database increases the speed of finding relationships between objects. Performance textual objects (contents, layouts, etc.) are stored directly in DGraph while an Amazon S3 object store stores any binary objects, such as images.
Tenants may define multiple data sources within the INTOUCH system. These data source definitions are maintained within the Asset Library and, therefore, can benefit from the same ownership and permissions rules as any other asset within the system. All pulled data, except for that which is bulk uploaded, is retrieved from REST calls to external systems defined by the tenant. INTOUCH maintains the definition of the REST call and its parameters while the data source maintains the fields expected within the response. The TLS protocol secures and encrypts these data sources.
Tenants have APIs available to them to create communications without user involvement. When desired, tenants may provide data within the transaction that is to be used in the creation of the communications. This data may be used directly as variable values or as keys to be used to pull the data from other data sources. The incoming transactions are secured and identified by tenant realm and user.
Used for generating communications in batch jobs; tenants make use of a REST call to upload bulk data files onto an Amazon Elastic Block Store (EBS) volume specific to a container linked to a tenant realm.
Prior to being rendered into their final form, communications are built and defined in a JSON structure that will contain both the structure of the communication as well as various useful metadata related to the content and purpose of the communication. This JSON structure is stored alongside the final rendering of the communication and may be used by the customers for a variety of purposes including indexing or fulfillment purposes.
The JSON structure and the final rendered format of the communications are stored within tenant-specific encrypted Amazon Simple Storage Service (Amazon S3, or S3) storage buckets.
To enable rapid lookups of communications via History functions, INTOUCH utilizes an Amazon OpenSearch index database. This index is maintained on an EBS volume that is specific to a tenant and encrypted with a tenant-specific key. This index maintains pointers back into the History maintained within S3.
Tenants’ customer data make personalization, automation and real-time interactive customer communications possible; it is a crucial business imperative to keep customer data secure and compliant, at all times, at every layer. INTOUCH provides multiple robust data security measures at every level.
INTOUCH applies all best practices to data privacy and security when handling imported private data: only a properly credentialed and entitled user can access data through the application, and data is always stored in a cryptographically encrypted form. INTOUCH, in combination with the cloud platform, ensures the security and privacy of tenants’ customer data.

AWS strategically places a limited number of access points in the cloud to allow for a more comprehensive monitoring of inbound and outbound communications and network traffic. These customer access points—API endpoints—allow secure HTTP access (HTTPS), that provides a secure communication session with storage or compute instances within AWS.
AWS has implemented network devices dedicated to managing interfacing communications with Internet service providers (ISPs). AWS employs a redundant connection to more than one communication service at each Internet-facing edge of the AWS network, with each having dedicated network devices. INTOUCH connects to an AWS access point via HTTP or HTTPS using SSL, a cryptographic protocol designed to protect against eavesdropping, tampering and message forgery.
AWS services support IPsec and SSL/TLS for protection of data in transit. IPsec is a protocol that extends the IP protocol stack, often in network infrastructure, and allows applications on upper layers to communicate securely without modification. SSL/TLS, on the other hand, operates at the session layer; and while there are third-party SSL/TLS wrappers, it often requires support at the application layer as well.
The AWS Management Console uses SSL/TLS between the client browser and console service endpoints to protect AWS service management traffic: encrypts traffic; authenticates data integrity; and employs the client browser to authenticate the identity of the console service endpoint by using an X.509 certificate. After an SSL/TLS session is established between the client browser and the console service endpoint, all subsequent HTTP traffic is protected within the SSL/TLS session.
INTOUCH also uses AWS APIs to manage services from AWS either directly from applications or third-party tools, via SDKs, or AWS command line tools. AWS APIs are web services (SOAP or REST) over HTTPS. SSL/TLS sessions are established between the client and the specific AWS service endpoint, depending on the APIs used, and all subsequent traffic, including the SOAP/REST envelope and user payload, is protected within the SSL/TLS session.
SSH is the preferred approach for establishing administrative connections to Linux servers. SSH is a protocol that, like SSL, provides a secure communications channel between the client and the server. In addition, SSH also supports tunneling, which INTOUCH uses when protecting the application session in transit.
As a security best practice, INTOUCH use HTTPS protocol to protect data in-transit. The SSL encryption and decryption operations can be handled by its AWS Enterprise Cloud Computing (EC2) instances. INTOUCH handles SSL termination using Elastic Load Balancing (ELB), which supports SSL termination. ELB can centrally manage the INTOUCH SSL certificates as well as encryption to backend instances with optional public key authentication.
INTOUCH load balances HTTP/HTTPS applications and sometimes uses IP layer 7-specific features, such as X-Forwarded and sticky sessions. INTOUCH also uses strict IP layer 4 load balancing for applications that rely purely on the TCP protocol.
Encrypting data at rest ensures the security of the data—even if an unauthorized party gains access to it—and increases the difficulty for an attacker to compromise data, even if they are able to compromise an endpoint.
Encryption is one of the most widely used techniques for protecting data at rest. AWS provides the ability to add an additional layer of security to customer data at rest in the cloud by providing scalable and efficient encryption features. AWS server-side encryption encrypts data after the API call is received by a service, leveraging the AWS Key Management Service (KMS) without the worry of managing and rotating keys since AWS automatically manages them.
INTOUCH’s source data comes from either a tenant’s connected system(s) or from an EC2 instance. INTOUCH can upload that data over a secure HTTPS connection to any of the AWS services that support automatic server-side encryption. The service endpoint handles the encryption and key management processes. For example, S3 and EBS support server-side encryption (SSE) of user data. Server-side encryption is completely transparent. INTOUCH databases use EBS storage so that all database storage is encrypted in this way.
The SSE-S3 and EBS process is how AWS manages the encryption keys. In this option, AWS generates a unique encryption key for each object, and then encrypts the object using AES-256. The encryption key is then encrypted itself using AES-256, with a master key that is stored in a secure location. The master key is rotated on a regular basis.
All data are isolated and secured during storage and transactions within the INTOUCH environment. When sensitive tenant customer data are collected, they are supplied in an encrypted format using keys specific to that tenant. The encrypted data packet is tagged according to the realm from which it was obtained.
INTOUCH employs a multi-realm authentication and authorization scheme that assigns each tenant a realm, or multiple realms, and isolates all operations and data by realm and user. INTOUCH authentication allows customers to use their own identity stores—such as LDAP or Active Directory—or default to the Topdown-provided store. Because of these flexible deployment capabilities, security administrators can control authentication and access to INTOUCH via tools with which they are accustomed.
INTOUCH gives tenants full control over their realms so they can set password policies and assign users to roles. For identity management, INTOUCH supports Single Sign-On (SSO), Federated Identity Management (e.g., using social media credentials), Identity Brokering, and also provides support for the standard protocols such as OpenID Connect, OAuth 2.0 and SAML 2.0.
At the application level, INTOUCH employs a hybrid approach based on Access Control List (ACL) and role-based access authorization to its functions and objects. Customers have direct control over the roles assigned to their users and may distinguish their users into various groups.
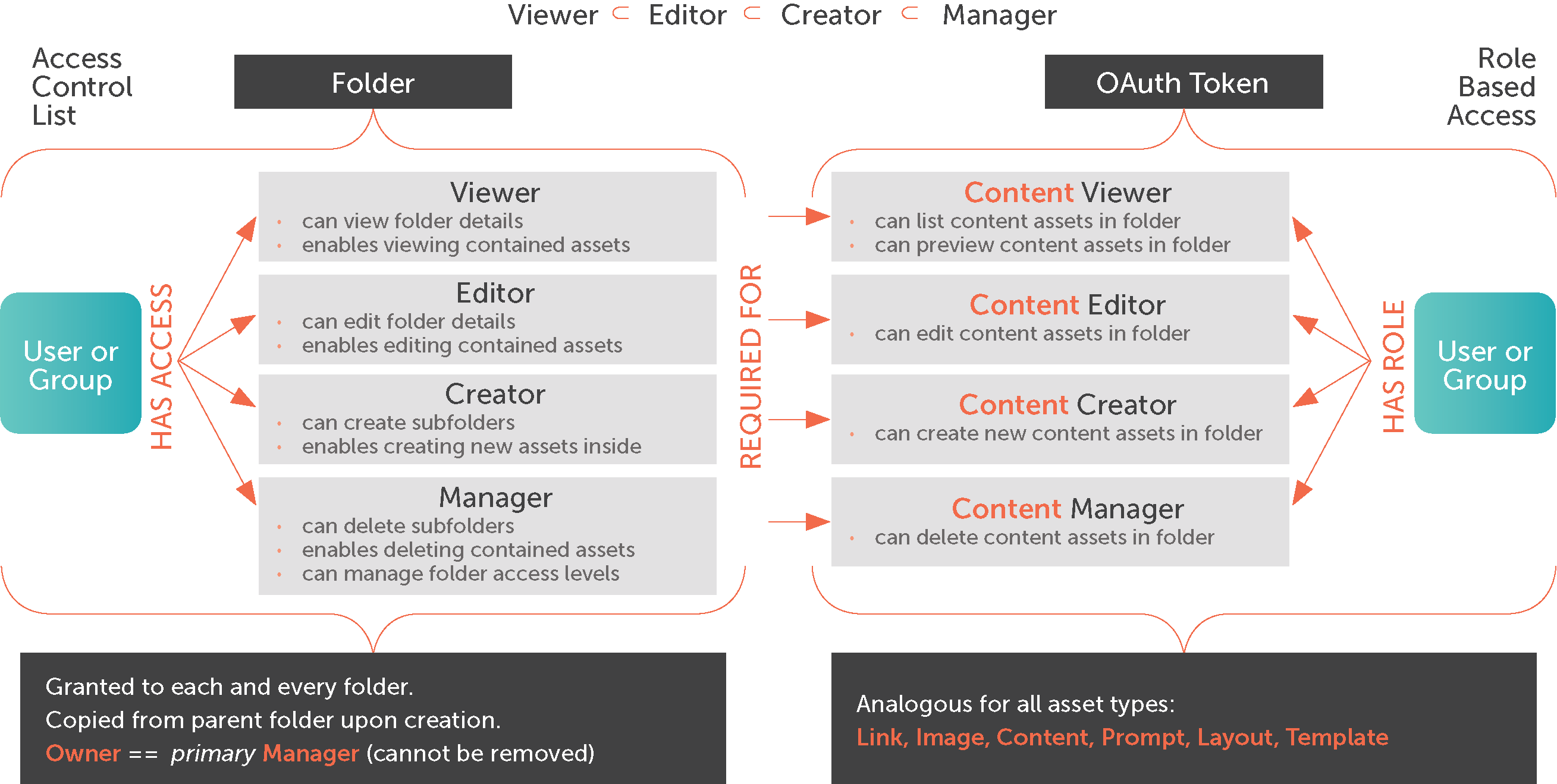
A tenant’s business administrators may give users the authority to author content, templates and layouts, business rules or other asset types by organizational or asset library (i.e., repository) structure. For example, they can organize the application by folders and subfolders for each organizational unit and then, within the folders, they can assign permission to what asset types a user can create, edit or delete. Users may also be restricted to communication creation based on organizational or Asset Library structure.
To ensure that data integrity is not compromised through deliberate or accidental modification, INTOUCH uses resource permissions to limit the scope of users who can modify the data. Even with resource permissions, accidental deletion by a privileged user is still a threat. INTOUCH performs data integrity checks—Message Authentication Codes (SHA-1/SHA-2), Hashed Message Authentication Codes (HMACs), digital signatures, or authenticated encryption (AES-GCM)—to detect data integrity compromised on key pieces of data. Should INTOUCH detect compromised data, INTOUCH restores the data from backup or to a previous version.
INTOUCH uses representative data whenever actual data are not directly required—for example, when sizing display or layouts of pages and communications. Sensitive in-the-clear data are limited to only those cases where their use is required for calculations or for final presentation. In those cases where data must be used in its clear form, Topdown employs best programming practices to ensure that sensitive data are isolated within a process and is immediately re-encrypted upon task completion.
INTOUCH has an added extra level of security—it maintains a container specific to each tenant. Almost all of a given tenant’s customer data that may contain PII, PHI, or other protected data is kept in this container. The EBS volume for the container is encrypted with a tenant-specific encryption key, accessible only via transactions authenticated into a tenant’s realm.
All communications which INTOUCH generates are stored in final format (e.g., HTML, PDF, etc.) in tenant-specific encrypted S3 buckets.
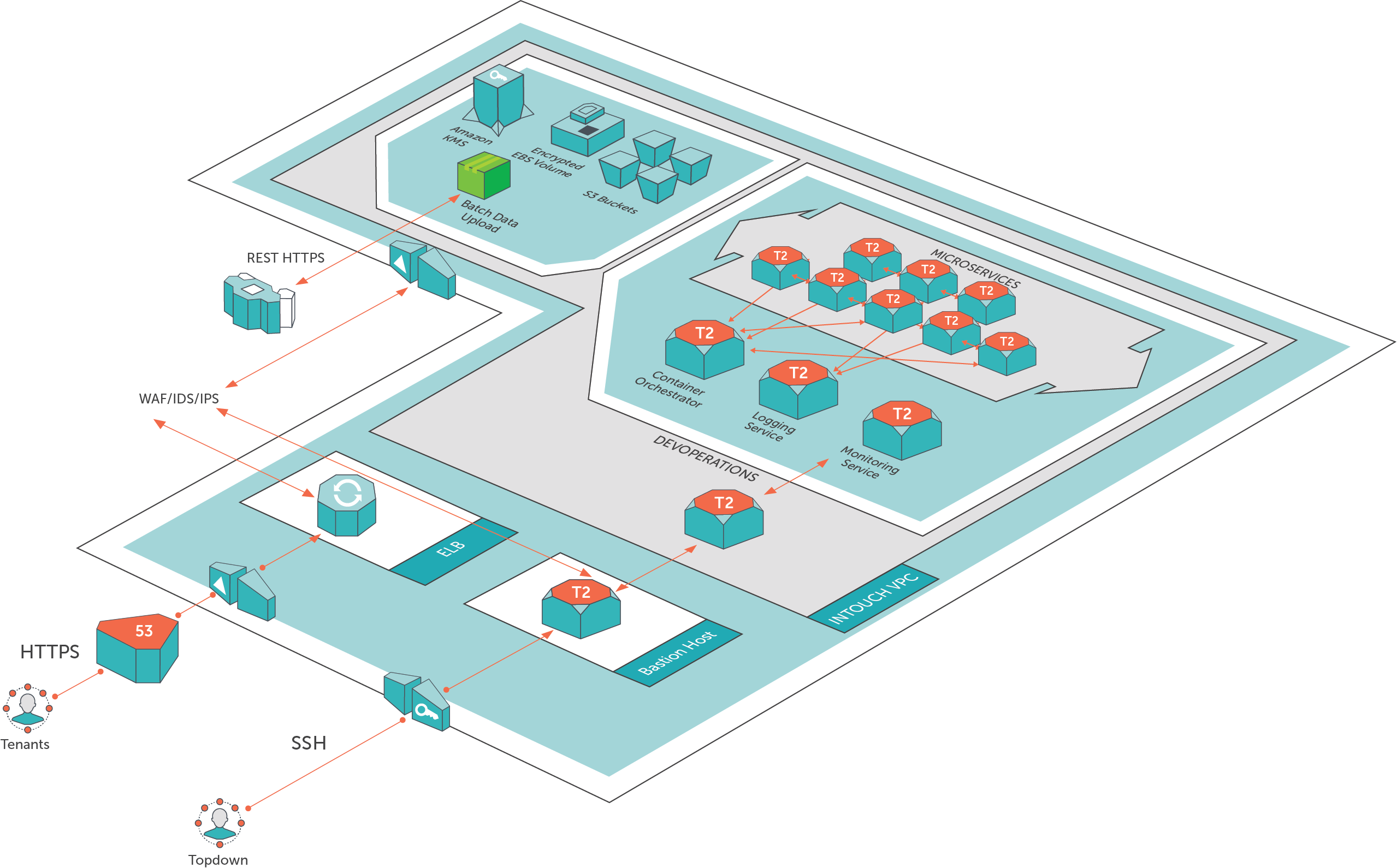
On the lower left is an SSH session into a Bastion host, the Topdown managed service provider's entrance into the system.
On the upper left corner are the containers INTOUCH sets up on a per-customer basis as an added layer of security for protecting the customer data that INTOUCH writes into final-format communications.
To learn more about the INTOUCH technology architecture, check out the technology architecture white paper.
Topdown has taken every possible step to secure the INTOUCH application and the customer data that tenants need to personalize their customer communications. Maintaining that security requires an ongoing effort by Topdown and our tenants. We take that obligation very seriously. By reading this white paper, we know that you do, too.
As you can see, Topdown has gone to great lengths to insure the security of the INTOUCH architecture and application.
Fill out our contact form if you would like to know more about INTOUCH, or to schedule a demonstration.