Cloud-Based CCM Security: Physical, Network, OS and Database Layers
Cloud-based CCM security is achieved in layers. In a previous post, Security Overview: Cloud-Based Customer Communications Management, we gave you a quick summary of each of the security layers: physical, network, operating system (OS), database and application. Let’s take a closer look at those first four tiers.
Security Layers:
- Physical layer: Even if everything is in the cloud, there are physical data centers somewhere hosting your data and apps. These data centers need backup schedules, access control, staff background checks, and so on.
- Network layer: This is where data moves, so it’s a layer ripe for vulnerabilities. Companies typically have firewalls, encryption, and other practices in place to ensure network security. Customers are affected by network security measures when they slow or prevent their interactions with the company, or when customers’ data are compromised.
- Operating system (OS) layer: OS security most strongly impacts employee users, who are usually required to securely log-in for access and may only be allowed to access certain systems from specified locations or devices.
- Database layer: This is where your cloud provider(s) keep(s) data pertaining to your account. To be a secure multitenant cloud environment, a cloud provider should maintain separations between clients and implement strict user access controls.
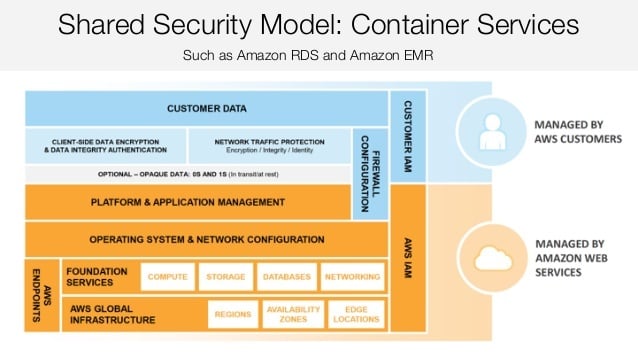
Our cloud platform partner, Amazon Web Services (AWS), is responsible for these levels of security for INTOUCH®, our new customer communications management (CCM) solution developed on and for the cloud. AWS provides a secure infrastructure for our SaaS application. AWS takes care of the facilities, physical security of the hardware, network infrastructure, and virtualization infrastructure. Under the Shared Responsibility Model for Container Services, which is the model we’re using for INTOUCH, AWS also manages OS and network configuration, along with some degree of platform and application management, depending on firewall configuration.
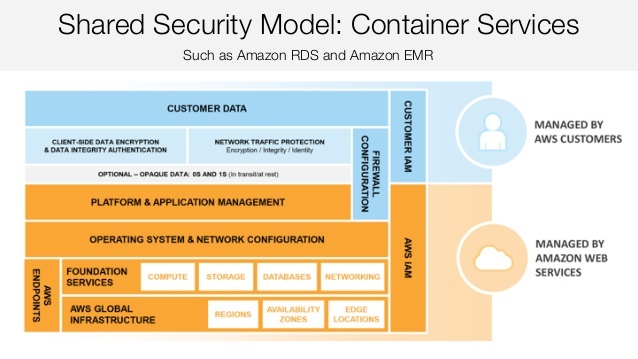 For security wonks, here’s how AWS explains it in its AWS Security Best Practices white paper:
For security wonks, here’s how AWS explains it in its AWS Security Best Practices white paper:
“The AWS shared responsibility model also applies to container services, such as Amazon RDS and Amazon EMR. For these services, AWS manages the underlying infrastructure and foundation services, the operating system and the application platform. For example, Amazon RDS for Oracle is a managed database service in which AWS manages all the layers of the container, up to and including the Oracle database platform. For services such as Amazon RDS, the AWS platform provides data backup and recovery tools; but it is your responsibility to configure and use tools in relation to your business continuity and disaster recovery (BC/DR) policy.
For AWS Container services, you are responsible for the data and for firewall rules for access to the container service. For example, Amazon RDS provides RDS security groups, and Amazon EMR allows you to manage firewall rules through Amazon EC2 security groups for Amazon EMR instances.”
Got that? It’s okay if you don’t – our developers get it, so we’ve got you covered.
What Does It Mean to You?
So what does this mean if you choose INTOUCH as your CCM solution? It means we pass the advantages of multi-layered security measures by one of the largest, most established cloud platform providers in the world directly to you when you adopt INTOUCH. By taking advantage of AWS’s existing security features, Topdown is able to develop powerful, scalable and affordable CCM software.
You can rest assured, as we do, that AWS has robust systems in place to limit access to its physical servers, detect intrusions, scan for malware, deter denial-of-service (DOS) attacks, and more. And they use top-of-the-line virtualization technologies at different layers – along with containers – to separate servers, OS images, etc.
Application Layer Security
We took advantage of AWS’s secure public cloud infrastructure, then supplemented it with our own application-level security measures. We’ll get into how we’re doing that in a future article, so be sure to subscribe to our blog to be notified when it’s published.